Internet self-defense guide
After talking with friends and family, I realized that a lot of them were not aware of some facts with the Internet, so let's take a look at 7 basics.
1 - Use HTTPS
A lot of misconceptions orbit around HTTPS. Nowadays, a lot of websites use it, you can easily recognize it by a small green lock in your web browser (see image). If someone is spying on the wifi network you are connected to, he won't understand what you say to the website.
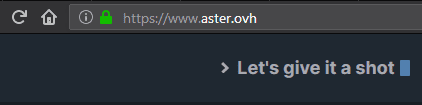
Using HTTPS means that the way you communicate with the website is secure, not that the website is secure. This is a huge difference.
A contrario, without HTTPS (the small green lock), if someone spies on a public network, he can get access to everything send through the network (passwords, credentials, confidential information, etc.).
Network security is defacto important. Use a strong password on your wifi router and pay attention to HTTPS especially on a public Access point (Fast Food, Hotels, etc.).
2 - Domain name
A way to spot malicious websites is to understand how a web address (aka URL) works. It is possible to dissect it in 3 parts.
Top-level domains
It is the suffix of the URL, perhaps you know some of them such .com, .org, .fr, .io, etc. For your information, every country has its own suffix. .fr is for France, .en for England and so on. But this part is not important about spotting malicious website.
Domain names
Every website is running on at least one server. A server doesn't have a name like Bob or Anne, but it has an IP address, an identifier. If you want to contact Google, you can search for http://216.58.204.110/ to reach one google server hosting the google webpage.
Remembering every IP address is painful and complicated, that's why domain name was created. It links a name to an IP address e.g. google.com is linked to http://216.58.204.110/.
There are official domain names such google.com and unofficial such go0gle.com or gooogle.com. Usually, companies buy similar domain names to prevent malicious usage. As you can guess, if someone uses a similar domain name of a famous brand or bank, he can easily copy the login page and fools you. You will think you are on the official page but in fact, you don't. The worst is: they can redirect you to the official website after you gave them your credentials.
Sub-Domain names
With a domain name, you can create as many sub-domain you want with whatever name you want. That is pretty cool because if your name is John Doe, you can name it like this: john.doe.com (.john is the sub-domain). And if you have a blog, you can do something like this: blog.john.doe.com.
What you need to be careful is: there are no official or unofficial sub-domain names. google.malicious.com is perfectly legal and can happen. So make sure to reach the
correct website with checking the domain name instead of the sub-domain!
For instance, I rent the domain name aster under .ovh top-level domain. If I want to add a photos.aster.ovh, I can and that's how it is working for a normal website.
Now, if a malicious person wants to fool you, he can rent malicious.com and create the sub-domain security-google e.g. security-google.malicious.com. And I can assure you it is not a google website.
It works exactly the same with mail address. You can probably trust security@facebook.com, but do not trust security-facebook@gmail.com.
3 - Sender of email
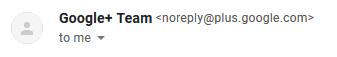
Whatever the email provider you have (Gmail, ProtonMail, Outlook, etc.), there are two different fields when you open an email: the name of the sender and the email address of the sender (see image below). This is very different because malicious people can modify their name (but not their E-mail address!).
What does it mean?
Let's say you get an email from Google. It will appear like on the image:
Google+ Team <noreply@plus.google.com>
But if someone wants to trick you, he can choose the same name as the Google team such as:
Google+ Team <security-team-googl@gmail.com> (if this email is available).
Do not open an attached file if you are not sure of the sender! Always check the e-mail address and if you can recognize it. It works the same with malicious people spoofing Google, Bank, Facebook, or whatever.
4 - Verify the link when clicking somewhere
When you see a link or a button, what is wrote can be different from the link it is hiding. For example, this link https://www.google.com doesn't go to Google but to an inexistent webpage.
I can replace my website with a copy of your bank login page, Facebook, ... and send you the link by e-mail. It is called phishing and this is really powerful. To spot the trick, check on the bottom left corner, you should see the real link appear when you hover the link with your mouse.
5 - Passwords
On the Internet, there are websites getting hacked and their data are leaked to everyone (including malicious people). Therefore, it is possible to find online email addresses with their associated passwords. Maybe yours as well. You should check on this website if your email/password is compromised. Here is my advice to have good passwords (resistant to guessing and brute force).
- Use lower and upper case ;
- Use alphanumerical letters ;
- Do not use word findable in a dictionary ;
- Do not reuse the same password in different websites.
I guess you do not have only 3 accounts but more like 40. So my advice is to use a password manager (such as KeePassXC, LastPass, 1Password, iCloud Keychain, etc.). They can help you to store your passwords in a digital fortress locked with a master password. You only have to remember one robust password and the password manager will take care of the big memory task. If you don't like to copy-paste every time, you can get auto-completion with web add-ons.
6 - Activate 2-Factor Authentication
Following the previous point, imagine a malicious person gets access to your password by luck (guessing it), brute force (trying 100000 times), or data leaks. If you activate two-Authentication Factors (2AF) in the settings, the malicious person cannot connect to your accounts without having access to your SMS, 2-FA application (Google authenticator, Authy, etc.) or email address for example.
2-AF prevents from an unauthorized connection. It is highly recommended to activate it for the above reasons.
Some games encourage the 2FA solution by giving gifts when you use it! But remember to use 2-FA with critical services like everything related to confidential data or money such as e-mails, banks, e-commerce, etc.
7 - Back-up your data
Have you ever heard about Ransomware? It is a kind of malware really used for several years. One very famous one was WannaCry, it took down a lot of old Windows computers running in companies, factories, etc.
Ransomware is a malicious software which encrypts the computer. You cannot read files anymore without a special key. Usually, the ransomware asks for a ransom in exchange for the key to decrypt your files. In a lot of cases, the key is not provided if you pay anyway.
Here comes the point: Do not pay ransomware. Instead, the good practice is to back-up your files every week/month (on an Hard-Drive) or sync them on the cloud (with Dropbox, Nextcloud, Google Drive, etc.). So, if you get caught with ransomware, just delete everything and get back all your files without problems.
A lot of ransomware propagate through attached files in email and illegal downloading.
TL; DR (Conclusion)
Too Long; Didn't Read, were you too lazy? Here is a sum-up of the 7 points.
- Use HTTPS whenever you can, especially on public wifi, but it doesn't mean the website is secure. So be careful when providing credentials.
- There is a difference between domain name and sub-domain name, don't be tricked!
- In an e-mail, it is very easy to change the sender name, trust only the sender e-mail.
- There is a difference between the appearance of a link/button and the real URL.
- Use Strong and different passwords.
- Activate 2-factor authentification on critical websites (main e-mail, banks, social media, etc.).
- Back-up your data offline or online in case of ransomware, hardware failure, etc.
I really hope you liked my first post and you learned at least something news.
Browse safe